Success Story
Introducing the first Security Program Management solution built with, by, and for the CISO Community.
Because the last thing you need is another tool to tell you what’s wrong, we help you manage the security plan, progress, and priorities so you can show what it takes to make it right for the business.
Blue Lava has been selected for the Microsoft for Startups Pegasus Program.
Blue Lava is thrilled to be actively involved in the Microsoft for Startups Pegasus Program, forging a strong partnership with Microsoft to accelerate our growth and success.
“We are grateful for the support and confidence Microsoft has shown in our vision, and we are excited about the transformative impact we can create together.”
David Walter
CEO, Blue Lava


Every business-critical function requires its own system of record…especially security.
“Before Blue Lava, we were living in spreadsheets and PowerPoints.” – CISO Fin Tech
The good news is, you don’t have to go it alone. Security leaders can now manage their program all on one SaaS platform.


Measure
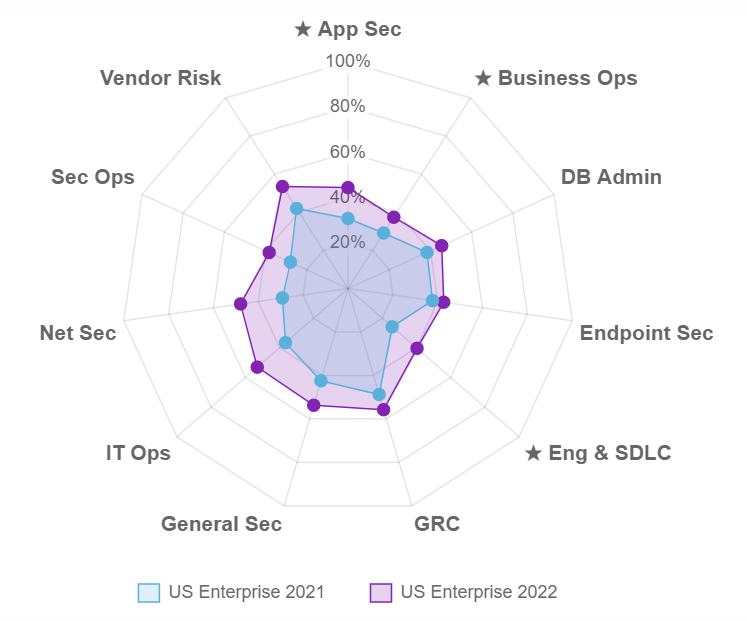
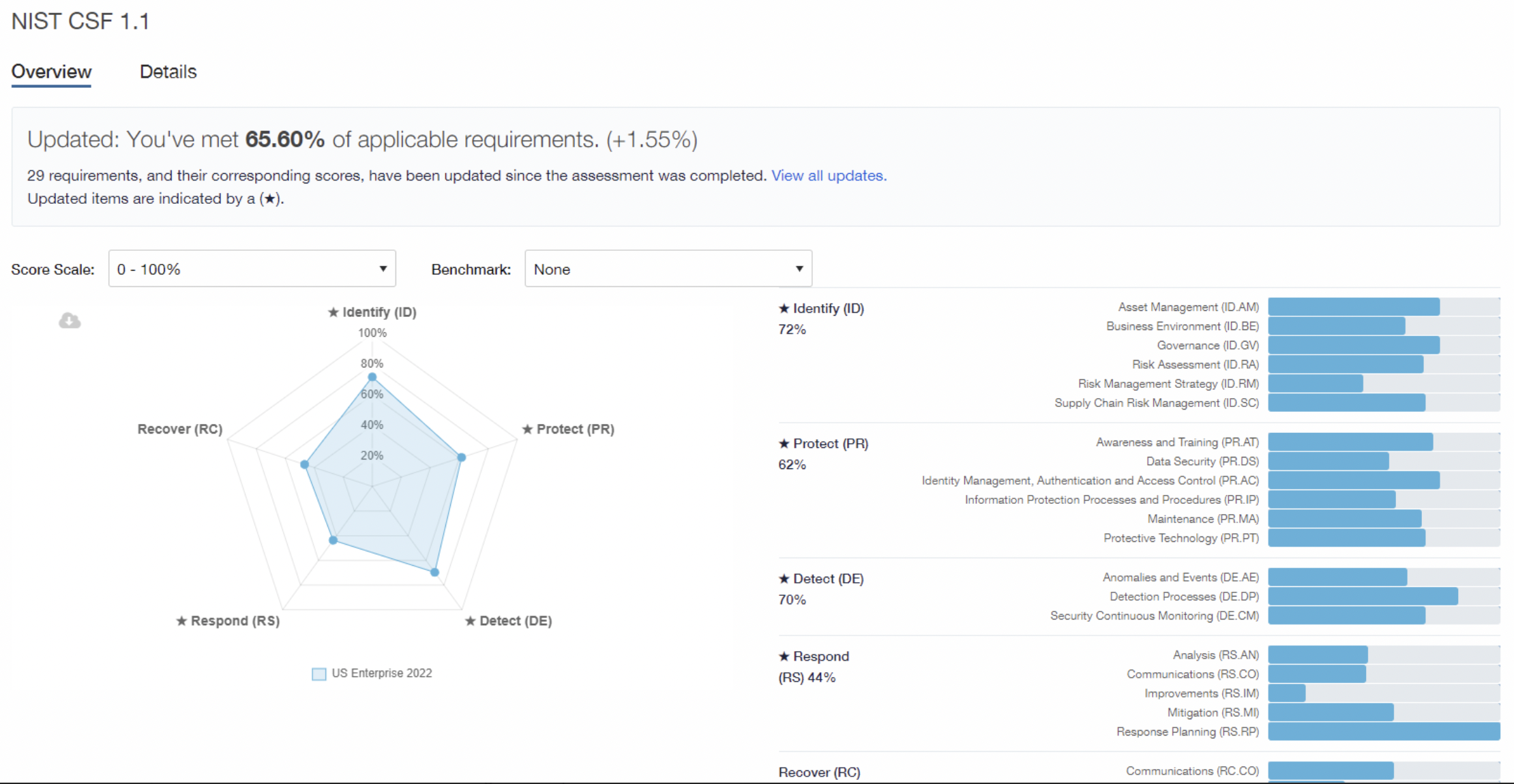
Take stock of the state of your security program – benchmark across people, processes, technologies and— quickly and effectively.


Optimize
Guide roadmap planning and investment decisions with recommendations that link business objectives, risk impact and resources required for success.


Communicate
Translate security speak into the language of business risk to engage stakeholders and build support from executives and the board.


Communicating to Executive Peers
“Our CEO stated, “This is the first time I understand what we’re doing in information security.'”
CISO, Global Medical Supplies Company


Success Story
Determining security priorities
“With Blue Lava, we now have a common language, a common guide for our global security program. Without the platform, it would have been just too complex. It takes me literally 5 minutes to log in and pull the data.”
CISO, Global Digital Services Company
Success Story
Planning and prioritizing to protect business and reputational risk
“Blue Lava was the first investment that I recommended because it provides me that ability to do an initial baseline assessment from which we can build upon as we move forward.”
VP and CISO,
Driven Brands
Success Story
Communicating to the Board
“Blue Lava provides me with the actionable and quantifiable insights necessary to confidently go to the Board and represent my program well.”
CISO, Cybersecurity Firm

Risk Analytics and Recommendations Engine
Our platform leverages the VERIS framework data standard underlying DBIR to help you align your security roadmap to the specific needs of your organization. Linking risks to security initiatives elevates the conversation, so you can focus on enabling the business.
Experience Automation and Real-time Reporting
Assess Maturity and Risk
Determine how well the business is protected and where the gaps are with pre-built guidance and recommendations against a variety of frameworks.
Compare and Prioritize Options
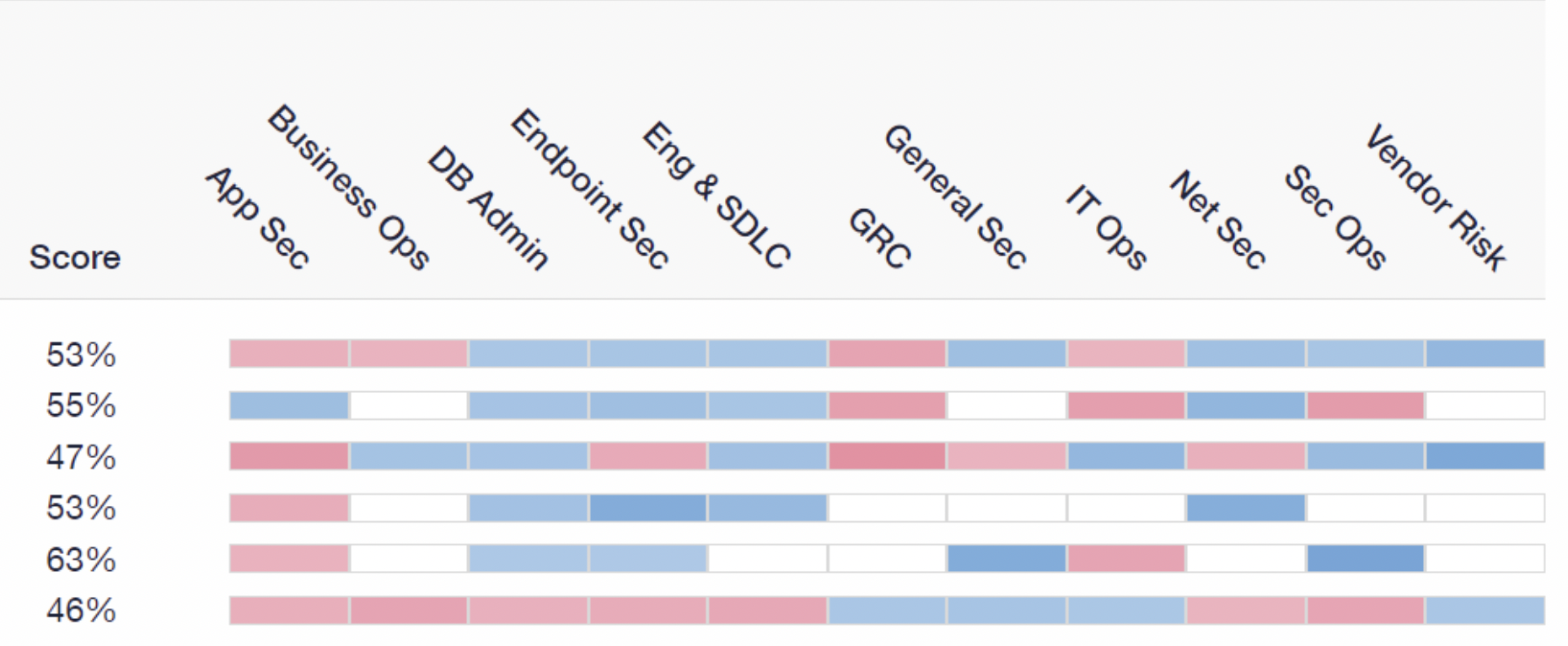
Simulate the impact of investment and prioritization scenarios and provide support for trade-off discussions backed by risk and peer benchmarking data automation.
Strategize and Plan
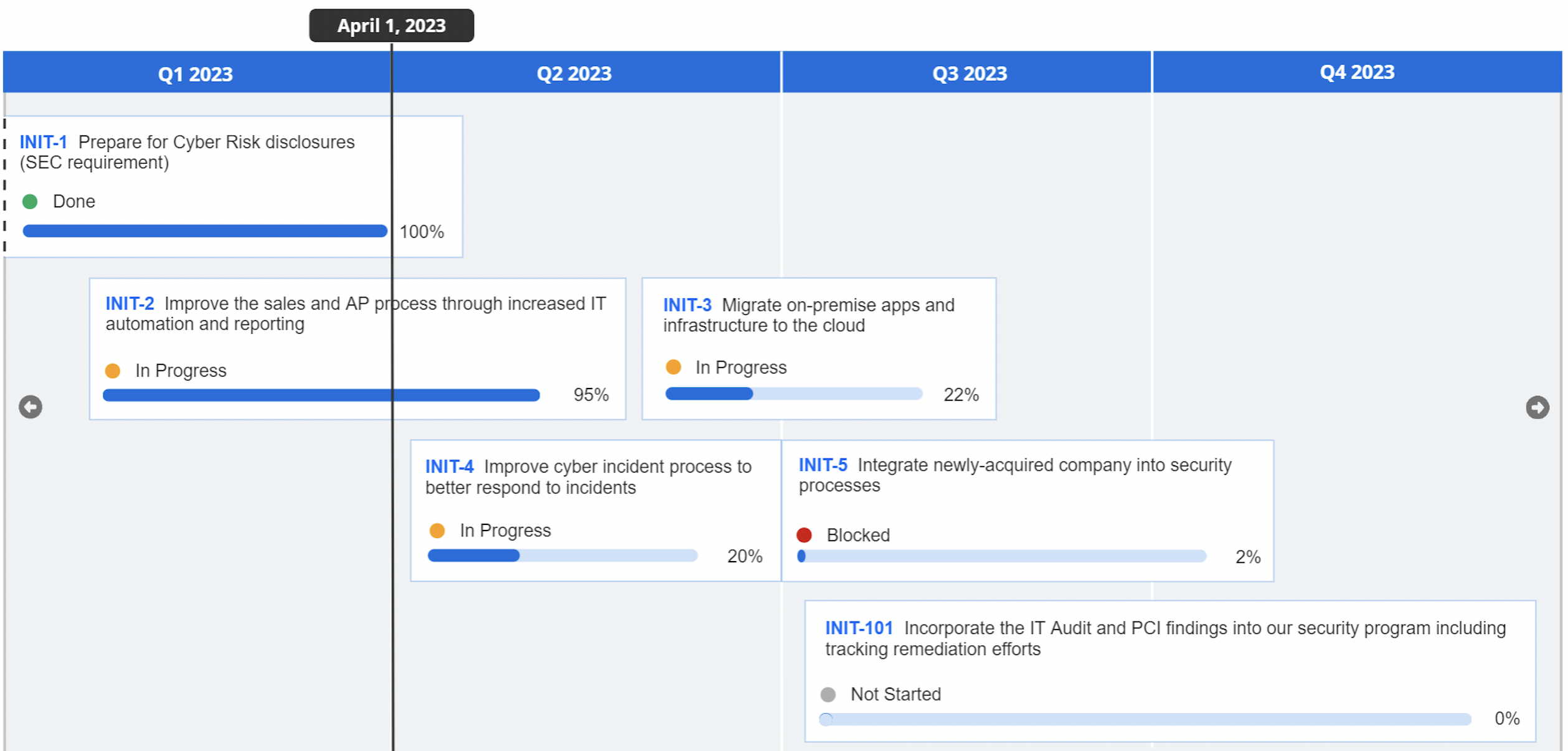
Centralize planning, prioritization, and tracking of strategic security initiatives with roadmap and action plans aligned to business objectives.
Engage and Inform
Create business and board-level reporting to engage executives and peers in discussions and convey the impact of security tradeoffs.
Featured resources
Security Program Management Platform
Blue Lava empowers security executives to easily measure, optimize, and communicate their security program in one place. Learn how you can transform the way you manage the business of security with Blue Lava.


Blue Lava Origin Story
Blue Lava founders Demetrios Lazarikos (Laz), Julia Tran, Jonna Melinauskas, and Andy Hoernecke join Sean Martin and Marco Ciappelii on a Their Story podcast with ITSP Magazine, to talk about their work with the security community to build a game-changing security program management platform.
Reporting Effectively to Your Key Business Stakeholders
While cybersecurity is managed by an organization’s information security team, the Board of Directors is ultimately responsible for oversight of the program and major risks. So, when this cybersecurity’s CISO needed to clearly and confidently report on its security posture and progress to the Board and other key executive stakeholders, they invested in the Blue Lava Security Program Management platform.