

Security Program Management (SPM) and Governance, Risk and Compliance (GRC): What’s the Difference?
Blog Post
Security Program Management (SPM) and Governance, Risk and Compliance (GRC): What’s the Difference?
Emily Shipman
November 18, 2022
Compliant but not Secure | The Difference and Why it Matters
Security programs bear many responsibilities, but chief among them is the duty to protect and promote the wellbeing of the businesses, consumers, and shareholders they serve. For many years, the necessity to achieve compliance has been the driving force behind security programs. But while GRC programs born from compliance are designed to help security leaders build trust with consumers and the public, they often don’t have the context necessary to serve a critical stakeholder: the business.
In this blog we’ll explore these differences and why it’s important to distinguish Governance, Risk and Compliance (GRC) and an emerging discipline in cybersecurity: Security Program Management (SPM).
What are the benefits of GRC?
While GRC has evolved significantly since its formal introduction nearly two decades ago, the premise remains the same. GRC is a discipline adopted to help organizations break through interdepartmental siloes to align on and streamline the people, processes and technologies managing governance, risk, and compliance. Large public organizations from highly regulated industries are especially keen on implementing formal GRC programs to satisfy regulatory or other 3rd party requirements.
GRC functions as a single pane of glass view for risk and controls across the organization, not just limited to security. By design, GRC tools attempt to take a broad view to provide an apples-to-apples comparison of risks across the organization, and therefore need to be highly configurable. With this least common denominator approach, GRC acts as an effective system-of-record compliance checklist for regulatory purposes as well as an enterprise risk register.
Beyond GRC initiatives that identify and implement controls to bring residual risk to an acceptable level, an Integrated Risk Management (IRM) platform automates the ongoing assessment, control evaluation, reporting and monitoring for a more sustainable risk and compliance program.
What is Security Program Management and why now?
As the name suggests, SPM is very specific to information security. This emerging discipline focuses on measuring, optimizing, communicating, and managing the business value of a cybersecurity program in a holistic, programmatic way.
From the lens of the modern security leader, compliance is not the endgame, but rather one of many objectives whose importance varies by industry. When a security function is led by or run exclusively through a compliance lens, it runs the risk of taking a narrow and reactive stance that limits its ability to provide its full value to the business. The security leader is focused on improving the maturity of their program to mitigate risk, supporting the organization’s business objectives as well as compliance. CISOs in particular are under the constant pressure to “do more with less” while also justifying where they choose to invest by showing the impact and results of these initiatives. In other words, good compliance alone does not equate to adequate information security.
Rather than one-and-done assessments focused solely on past control performance, an automated SPM platform can help CISOs maximize results by assessing and tracking over and under investment across security disciplines to help plan and prioritize future initiatives. By mapping projects that directly address cybersecurity risks and benchmarking where they are against their peers, a SPM platform also enables security leaders to make more informed decisions by planning for the future and demonstrating how these investments directly impact the business over time.
With the ever-growing complexity of doing business in our increasingly digital world, information security is not only about being compliant but also defending against constantly emerging cybersecurity threats and enabling the business for growth. A security leader cannot rely solely on a risk and controls register; they need SPM in order to provide critical insights and continuous improvements.
Whether establishing a baseline assessment, introducing a new digital product, preparing for an expansion, or preparing to go public, there are common disciplines a security team needs to excel in to prepare for these initiatives that are not compliance or regulatory driven. For example, if the business is introducing new software products to enter an emerging market, how do they plan to build trust (compliance / SOC 2) and protect the data (invest into security products, e.g., encryption, etc)? ?
How do GRC and SPM intersect, and why are they considered separate disciplines?
In light of ubiquitous digitization of every industry and sector and highly publicized data breaches, cybersecurity has become an increasingly visible and important component to the overall risk profile of a business. Highly regulated organizations for example, are required to provide a framework to demonstrate their data is secure and rely on their information security teams to be compliant. Cybersecurity risk, however, is a very real concern for both strongly and less regulated industries and the markets they serve. For these reasons, it’s easy to understand why compliance risk and security risk intersect, though there are also very important distinctions between the two disciplines.
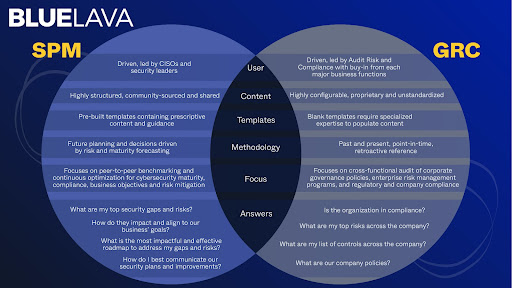

While there are many commonalities in terms of data collected for GRC and SPM, the objectives are distinctively different.
GRC offers compliance, SPM offers a plan
GRC programs are essential and necessary to help organizations create a strategy for managing the interdependencies between corporate governance policies, enterprise risk, and regulatory compliance. GRC does not, however, act as a planning tool to help guide organizations on where to go in the future. It is a retroactive process; reporting a point-in-time of what controls were in place, what were and were not effective, and what failures exist.
SPM on the other hand, is about looking at where you are, where you wish to go, and the progress that’s being made. InfoSec’s premise is driven by the need to proactively protect an organization from constant and ongoing threats, whereas GRC is driven by the need to report on and satisfy external requirements.
SPM is designed for cybersecurity
Highly configurable for general purpose use, GRC content (when offered) is often catered to operations and is not designed for security-specific use cases or needs. A purpose-built SPM platform contains workflow algorithms and hundreds of hours of pre-structured content mapped to a risk register for peer-to-peer benchmarking of common risks and specific actions that can be taken to address them. This cybersecurity intelligence and prescriptive guidance is built in – no need to manually create findings or map them to risks.
SPM is community-sourced
A highly regulated organization’s GRC program is largely treated as proprietary and confidential. By contrast, using industry frameworks and best practices, the SPM platform and processes were built with, by, and for the CISO to promote knowledge sharing and continuous improvement of the community as a whole.
SPM is led by the CISO and security team
A GRC program requires business champions from each major business function and is typically not controlled by the CISO or security department. This can result in complex, multi-year engagements that may not keep pace with the needs of the security program. On the other hand, SPM is led and managed by the CISO and the cybersecurity team.
It’s about time
In summary, while there are many commonalities in terms of data collected for GRC and SPM, the objectives are different. GRC documents what has transpired, and provides important information to assess status, prove compliance and understand where you are as an organization. SPM is a plan for the future, prioritizing initiatives based on what lies ahead, and the steps required to get there.
Why Blue Lava for Security Program Management
Blue Lava’s SPM is designed to be a proactive planning tool for the CISO or equivalent security leader to assess where an organization’s security program is today, and help it prepare for where it needs to go in the future. As a pioneer in this space, Blue Lava helps its extensive security leadership community better manage their programs and mitigate common risks. By understanding your roadmap, your resources, your business objectives and your timelines, the platform acts as an automated planning tool for continuous assessment, optimization and communication as initiatives are carried out.
Taking a compliance-based approach is no longer enough to simply keep your business out of trouble. To help the organizations they support grow and thrive, security leaders need the right tools to help prepare and protect them. Cybersecurity is becoming too complex and important to be managed by spreadsheets, or to be driven primarily by compliance.
If you want to see what Security Program Management can do for your organization, get in touch with us and we will arrange a live demo of Blue Lava’s SPM platform for you.




