

Part Three: Conclusions and Recommendations
Blog Post
Part Three: Conclusions and Recommendations
Demetrios Lazarikos (Laz)
July 7, 2022
This is the third of three blog posts about our recent survey on security program management. The previous posts discussed some of the survey findings about current practices and priorities for making SPM better. This one reviews conclusions and recommendations from the report.
The full report is available here: Security Program Management: Priorities and Strategies.
The previous two blog posts in this series presented some of the data from our survey of security program management current practices and priorities for improving SPM. But what conclusions can we draw from this data, and what recommendations can we make?
1. Organizations need ongoing visibility into the effectiveness of their security programs
Data: Almost two-thirds of the security leaders queried in our survey report that their organizations assess the maturity and effectiveness of their security programs infrequently (about once a year: 20%) or on an ad hoc basis (when required by an audit or special event: 19%; each group determines when to assess its own activities: 26%). Only 22% assess their progress several times a year, and 13% “continuously or every time the program changes.”
Recommendation: Ongoing visibility into security program effectiveness enables security leaders to continuously improve performance and react to changing conditions and new threats. Organizations that assess the maturity and effectiveness of their security programs infrequently or on an ad hoc basis should move to frequent or even continuous updates.
2. Security teams that rely on compliance standards should consider frameworks developed by security practitioners for security teams
Data: A large majority of organizations measure their security programs based on one or more of the main compliance standards, in particular NIST standards (75%), ISO 27000 (48%), PCI DSS (34%), and the EU GDPR (32%). Frameworks created specifically to assess and manage security programs are less widely used: frameworks created by the organization’s security group (25%), frameworks developed by consulting firms or security vendors (21%), and frameworks developed by different groups within IT (11%).
Recommendation: Frameworks and tools developed by security practitioners specifically for security program management provide more functionality for assessing and managing security programs and more guidance on best practices. Organizations should strongly consider using SPM-specific frameworks and tools to manage their security programs, especially those frameworks and tools that are designed to help organizations satisfy regulatory standards as an outcome of improving security.
3. Security leaders need better tools to track, analyze, and present security program data to management
Data: Three-quarters of the survey respondents reported that security leaders in their organization meet with their board of directors quarterly (37%) or monthly (40%). That is great for visibility and influence, but it creates a lot of work for security leaders, since the median time allocated to compiling data and preparing presentations is one to two weeks per meeting.
This can be quite costly, as illustrated by the back-of-the-envelope calculation below. This shows that a security team that meets monthly with the board may in effect be spending more than $100,000 per year just to prepare and present data at these meetings. It can be argued that the opportunity costs are even higher, since the value to the organization of the time of CISOs and hard-to-find senior security experts is usually greater than their compensation.
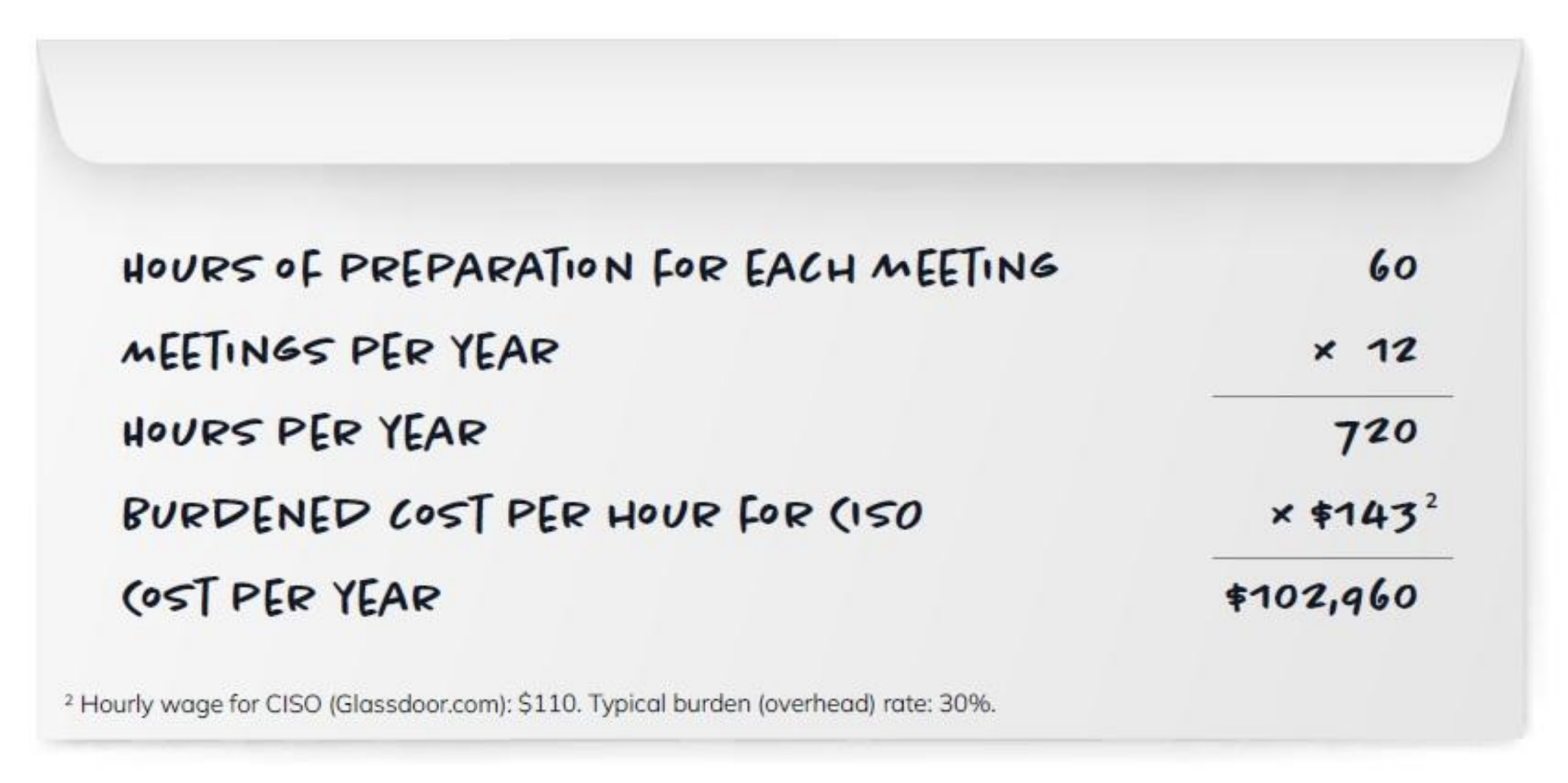

Recommendation: Tools that automate the collection, organization, and presentation of security program data for management reviews typically have a big payoff. Not only do they save security leaders weeks of their time each year, they can also present the data in ways tailored to non-technical executives, for example by generating comparisons with other organizations in the same industry. Organizations should utilize tools specifically designed to track, analyze, and present security program data to management.
4. Security leaders need tools to automate routine program management activities
Data: Security leaders feel they are spending too much time on important but relatively routine security program management activities. When asked about a list of nine program-related tasks, respondents were most likely to say they were spending too much time on preparing reports (38%), establishing policies and procedures (38%), and managing assessments (32%).
Recommendation: Security program management tools automate and streamline many security program management activities, including data collection, data analysis, tracking of security performance, comparisons across business units, report preparation, and policy selection based on industry best practices. Organizations should utilize tools that automate routine program management activities, while also helping generate insights on how to improve the organization’s security posture.
5. Security teams should invest in the six SPM activities where improvements would be most valuable
Data: Based on a list of eleven key security program management activities, security leaders most listed the areas where improving their organization’s capabilities would be valuable or very valuable. The top six:
- Collecting security data in an efficient manner
- Benchmarking security performance against industry peers
- Defining a roadmap of security initiatives and investments
- Implementing the security roadmap
- Identifying and prioritizing risk
- Maintaining a central record for data on security effectiveness
Recommendation: There are many ways that security teams can improve their security programs. Often it is difficult to prioritize the opportunities. The survey data provides insight into what areas peer security leaders think are the most valuable. Organizations should consider if their priorities are similar, and if so, invest in staff, tools, and processes to strengthen their performance in these areas.
Ready for more data and analysis on security program management practices and priorities? Download the full report at: Security Program Management: Priorities and Strategies.




